A new study describes a technique that rejuvenates aging blood-forming stem cells and could help reduce the risk of age-related blood disorders.



For decades, astronomers have been watching WOH G64, an enormous heavyweight star in the Large Magellanic Cloud, a galaxy visible with the naked eye from the Southern Hemisphere. This star is more than 1,500 times larger than the sun and emitting over 100,000 times more energy. For a long time, red supergiant WOH G64 looked like a star steadily reaching the end of its life, shedding material and swelling in size as it began to run out of fuel.
Astronomers didn’t think its final demise would happen anytime soon, because no one has ever seen a known red supergiant die. But in recent years, astronomers—including our team working with the Southern African Large Telescope (SALT)—discovered that this star has started to change, growing dimmer than before and seemingly warmer. This has surprised scientists and suggests the star’s final stages of life may be more complicated, and perhaps unfold faster, than once thought.
Massive stars, more than about eight times the mass of the sun, produce so much energy, which we see as light, that they run out of fuel within millions of years, instead of the billions of years of the sun’s lifespan.
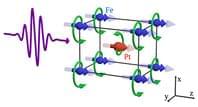
A century ago, Einstein and de Haas observed the transfer of spin angular momentum to mechanical rotation. It remains, however, unknown how the Einstein-de Haas effect operates at ultrafast timescales and atomic length scales. The authors use here time-dependent density functional theory combined with nuclear dynamics to investigate how ferromagnetic FePt reacts when irradiated by a femtosecond laser. They find that ultrafast loss of electronic spin angular momentum leads to generation of phonons carrying angular momentum, in a transfer process mediated by spin-orbit interaction.
I sat down with Dario Amodei in Bangalore. He built Claude, but he started as a biologist looking for a tool to cure disease. Today, he’s at the helm of an AI revolution that he compares to a tsunami society is actively ignoring. We got into the heavy stuff: why Anthropic secretly withheld a working model before ChatGPT existed, whether AI is on the verge of consciousness, and if outsourcing our thinking is going to make humans measurably stupider. Dario makes the case that coding is a dying skill, critical thinking is our last real edge, and the absurd concentration of power in AI right now is a massive problem, even though he’s one of the people holding it.
00:00 Introduction.
06:13 Scaling laws explained simply.
13:27 Trust, humility, and corporate motives.
22:44 Using Claude personally, AI knowing you.
31:03 Rich people criticizing their own system.
37:05 India’s role and IT partnerships.
44:15 Will AI surpass humans at everything.
50:17 Career advice for young Indians.
56:38 Open source vs closed AI models.
1:02:40 Biotech as the next big bet.
#NikhilKamath Co-founder of Zerodha and Gruhas.
Host of ‘WTF is’ & ‘People By WTF’ Podcast.
Twitter: https://twitter.com/nikhilkamathcio/
Instagram: / nikhilkamathcio.
LinkedIn: https://www.linkedin.com/in/nikhilkam… / nikhilkamathcio #Darioamodei LinkedIN–
/ dario-amodei X — https://twitter.com/DarioAmodei Instagram —
/ dario.amodei Watch ‘WTF is’ Podcast on Spotify https://tinyurl.com/4nsm4ezn Watch ‘People by WTF’ Podcast on Spotify https://tinyurl.com/yme92c59 Watch ‘WTF Online’ on Spotify https://tinyurl.com/4tjua4th #WTFiswithnikhilkamath #PeopleByWTF #WTFOnline.
Facebook: / nikhilkamathcio.
#Darioamodei.
LinkedIN-/ dario-amodei.
X — https://twitter.com/DarioAmodei.
Instagram — / dario.amodei.
Watch ‘WTF is’ Podcast on Spotify.
https://tinyurl.com/4nsm4ezn.
Watch ‘People by WTF’ Podcast on Spotify.

One of the largest known stars in the universe underwent a dramatic transformation in 2014, new research shows, and may be preparing to explode. A study led by Gonzalo Muñoz-Sanchez at the National Observatory of Athens, published in Nature Astronomy today, argues that the enormous star WOH G64 has transitioned from a red supergiant to a rare yellow hypergiant—in what may be evidence of an impending supernova.
The evidence suggests we may be witnessing, in real time, a massive star shedding its outer layers, shrinking as it heats up, and moving closer to the end of its short life.

A discovery by UCLA organic chemists may one day put catalytic converter thieves out of business. In new research, they’ve used abundant, inexpensive phosphorus as a catalyst in chemical reactions that usually require precious metals like platinum, one of the metals targeted in theft of the automotive components that convert chemicals in vehicle exhaust into less harmful forms.
This advance, however, will likely be more useful in the pharmaceutical industry and could one day help bring down the price of some drugs.

At the heart of the new discovery is amyloid precursor protein (APP), a protein that plays important roles in brain development and synaptic formation. Abnormal processing of APP can lead to the production of amyloid‑beta peptides, which play a central role in the development of Alzheimer’s disease. The scientists found that how APP is trafficked also controls whether a neuron forms amyloid-beta 42.
During the synaptic vesicle cycle — a fundamental process that underlies every thought, movement, memory or sensation — levetiracetam binds to a protein called SV2A. This interaction slows down a step in which neurons recycle synaptic vesicle components from the cell’s surface. By pausing this recycling process, the drug enables APP to remain on the cell’s surface longer, diverting it away from the pathway that produces toxic amyloid‑beta 42 proteins.
“In our 30s, 40s and 50s, our brains are generally able to steer proteins away from harmful pathways,” the author said. “As we age, that protective ability gradually weakens. This is not a statement of disease; this is just a part of aging. But in brains developing Alzheimer’s, too many neurons go astray, and that’s when you get amyloid-beta 42 production. And then it’s tau (or ‘tangles’), and then it’s dead cells, then dementia, then neuroinflammation — and then it’s too late.”
To effectively prevent Alzheimer’s symptoms, high-risk individuals would need to begin taking levetiracetam “very, very early,” the author said, possibly up to 20 years before the new FDA-approved Alzheimer’s disease test would even capture mildly elevated levels of amyloid-beta 42.
“You couldn’t take this when you already have dementia because the brain has already undergone a number of irreversible changes and a lot of cell death,” the author said.
Leveraging its status as an FDA-approved and widely used drug, the team mined existing human clinical data to investigate whether Alzheimer’s patients who took levetiracetam experienced slowed cognitive decline. They obtained clinical data from the National Alzheimer’s Coordinating Center and conducted a correlative analysis, finding that Alzheimer’s patients who took levetiracetam were associated with a significant delay from the diagnosis of cognitive decline to death compared to those taking lorazepam or no/other anti-epileptic drugs. ScienceMission sciencenewshighlights.
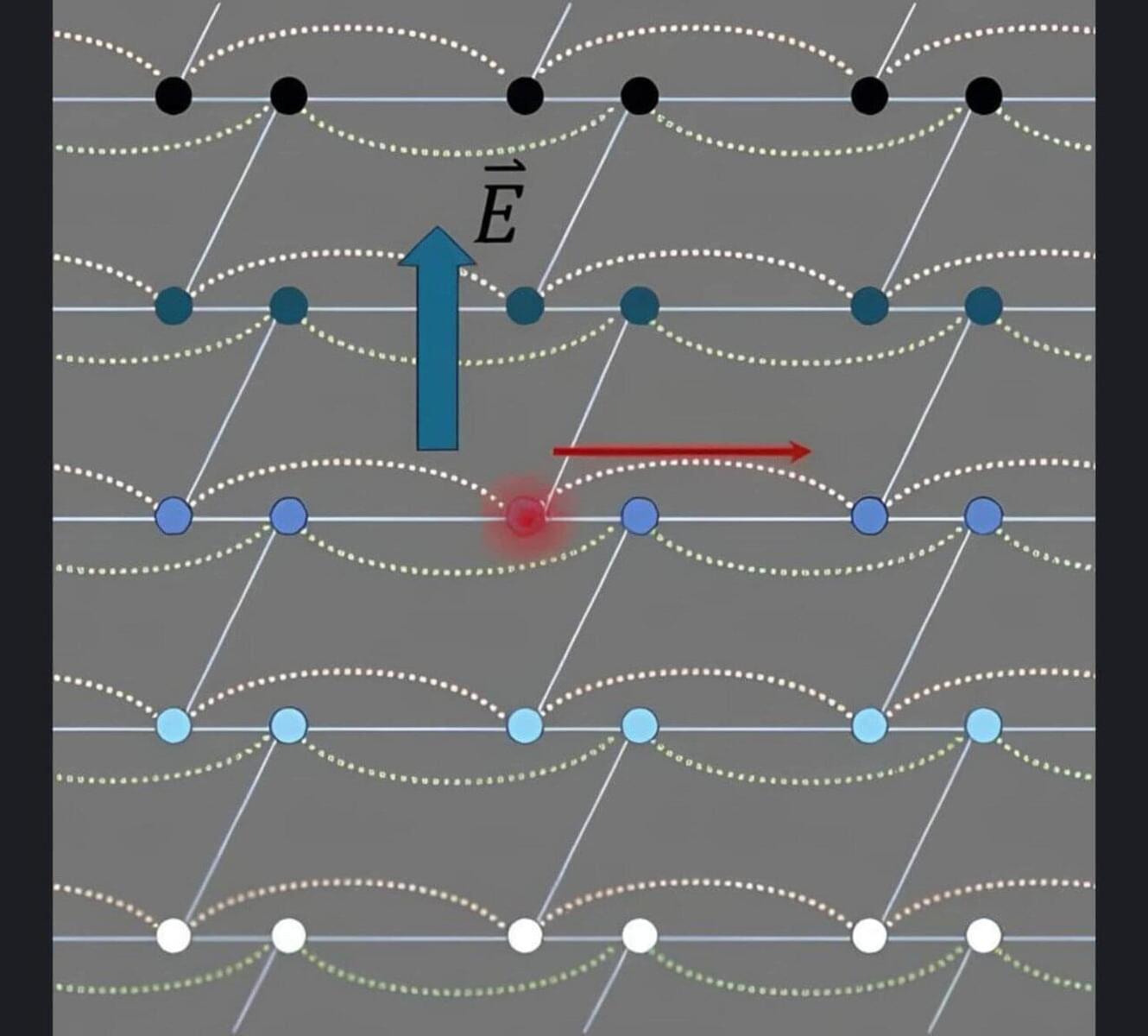
In physics, the classical “Hall effect,” discovered in the late 19th century, describes how a transverse voltage is generated when an electric current is exposed to a perpendicular magnetic field. Simply put, the magnetic field causes the electrons, which are negatively charged, to drift sideways, creating a negative charge on one edge of the conducting strip and a positive charge on the opposite side.
For decades, this voltage difference has been used as a diagnostic tool to measure magnetic fields with precision and characterize material doping levels, that is, the addition of a tiny, controlled amount of impurity to a pure material to change how it conducts electricity.
In the 1980s, experiments at ultra-low temperatures with ultra-thin conductors—imagine a sheet of paper—revealed that under intense magnetic fields, this voltage difference increases not in a straight line but in perfectly defined steps.

Kostas Pantopoulos & team find mice that lack IRP1 have altered energy metabolism and are protected against metabolic syndrome pathologies:
The figure shows liver in Irp1-/- mice fed a high-fat diet have reduced fat content; stained with oil red O. MetabolicSyndrome.
1Lady Davis Institute for Medical Research, Jewish General Hospital and Department of Medicine, McGill University, Montreal, Quebec, Canada.
2Department of Biochemistry, Microbiology & Immunology, University of Ottawa, Ottawa, Ontario, Canada.
3Institute for Research in Immunology and Cancer, University of Montreal, Montreal, Quebec, Canada.

Norway is implementing technologies to improve underwater sensing. Specifically, a development by the Norwegian company Kongsberg is cited as an example. Kongsberg claims to have created a device that “changes the way the Navy collects intelligence in the underwater environment.”
This is an upgrade to the Argeo Listen platform. The upgrade consists of an enhanced passive electromagnetic sensing system. This reportedly allows for more efficient detection of underwater objects with more precise measurements, followed by mapping.