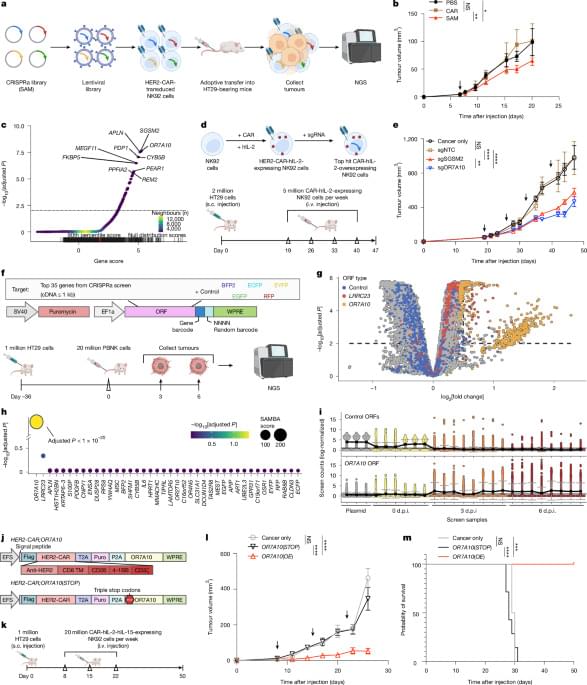
The identification of ‘boosters’ that drive gene overexpression directly in a CAR construct provides a simple and scalable strategy for developing effective CAR-NK cell therapies for solid tumours.


For centuries we treated technology as a tool, and now a new movement insists it is becoming the future of the human species itself.
Transhumanists like Harari and Kurzweil predict the merger of humans and machines, even the rise of a “digital God.” But critics fear this proposed future, calling transhumanism “the world’s most dangerous idea.”
Is the future one where technology is not merely a source of innovation but the basis for a new account of what it is to be human, or are claims of eternal life and new forms of intelligence just fanciful nonsense?
Joining the debate are transhumanist pioneer Zoltan Istvan, physicist and consciousness researcher Àlex Gómez-Marín, philosopher of mind Susan Schneider, and Softmax co-founder Adam Goldstein.
Tap the link now to watch the full debate.
We have for centuries sought technological progress. But now some are making the radical claim that technology is the future of the human race. ‘Effective accelerationists’ have won high-profile Silicon Valley support and claim we should accelerate technology to.

A new University of California San Diego study published in Cell challenges a long-standing assumption about how animal viruses become capable of sparking human epidemics and pandemics. Using a phylogenetic, genome-wide analysis across multiple viral families, researchers report that most zoonotic viruses—infectious pathogens that spread from animals to humans, including the cause of COVID-19—do not show evidence of special evolutionary adaptation before spilling over into humans.
“This work has direct relevance to the ongoing controversy around COVID-19 origins,” said Joel Wertheim, Ph.D., senior author and professor of medicine in the Division of Infectious Diseases and Global Public Health at UC San Diego School of Medicine.
“From an evolutionary perspective, we find no evidence that SARS-CoV-2 was shaped by selection in a laboratory or prolonged evolution in an intermediate host prior to its emergence. That absence of evidence is exactly what we would expect from a natural zoonotic event—and it represents another nail in the coffin for theories invoking laboratory manipulation.”

AFib AF
Atrial fibrillation (AF) is the most common arrhythmia and is a leading cause of stroke and heart failure yet often remains undiagnosed. Screening has been proposed to identify asymptomatic AF and initiate preventive treatment, but evidence for reduction in hard clinical endpoints such as stroke and heart failure remains inconclusive. In this state-of-the-art review, we critically examine major AF screening trials across opportunistic, systematic and consumer-driven strategies, focusing on design features, population selection, monitoring strategies and outcomes. Variability in trial design, particularly in randomisation timing, participation rates and intensity of monitoring, significantly affects both AF detection and clinical outcomes. Systematic screening shows promise, but many trials were underpowered for hard outcomes.


Astrophysicist Katy Clough uses supercomputers to simulate conditions at the start of the universe and other strong gravity regimes, such as around black holes, testing the limits of general relativity and the standard model of particle physics. Known as numerical relativity, these models are \.

Want to support our production? Feel free to join our membership at https://www.youtube.com/BeeyondIdeas/join.
Special thanks to our beloved YouTube members this month: Powlin Manuel, Saïd Kadi, Chenxi, Lord, Sudhir Paranjape, Nate Lachae, Alison Rewell, Thomas Lapins, Ahmad Salahudin, Antonio Ferriol Colombram, Anton Nicolas Burger 🚀🚀🚀
Experts featured in this video include Demis Hassabis, Tristan Harris, Aza Raskin, Elon Musk, David Deutsch, Michio Kaku, Brian Greene and Nick Bostrom.
Chapter:
0:00 A dangerous truth?
1:29 AI advancement.
3:46 AI pretending not to know.
7:29 Interactive tutoring.
9:37 That’s it from our sponsor!
10:21 The merging of QC and AI
12:03 IBM 100,000 qubits.
14:34 AI wipes out humanity?
16:05 Google Willow.
17:06 The misuse of AI and QC
18:22 Singularity and Turing test.
22:51 Reverse Turing test.
29:39 Quantum-AI consequences.
32:25 The double slit experiment.
36:15 Quantum multiverse.
41:05 Computing history.
46:49 AGI timeline.
51:45 Philosophical consequence.
#AI #quantumcomputing #singularity

Studies of the putative functional relationships between the gut microbiota and host cardiometabolic diseases (CMDs), including atherosclerosis, diabetes, and metabolic dysfunction-associated steatohepatitis (MASH), have garnered unprecedented attention in recent years.1,2 Although causality has not yet been unequivocally established, interventions targeting the gut microbiota, such as antibiotics and fecal microbiota transplantation, have been demonstrated to improve health.3 Although such interventions show unique clinical value in specific scenarios such as recurrent Clostridioides difficile infection,4 they typically show interindividual variability in efficacy and raise safety concerns, altogether underscoring the need for safer, more precise, and targeted strategies.5 A deeper understanding of the molecular mechanisms by which gut microbiota exert their functions in health and disease will be crucial to such goals.
Enzymes are intracellular proteins that perform defined biological processes, and enzyme-targeting drugs constitute a significant proportion of current therapeutics.6 In recent years, growing evidence has indicated that gut microbial enzymes are key mediators of microbiota-derived functions.7 Such enzymes contribute to CMDs pathogenesis primarily through 3 mechanisms: generating bioactive metabolites that influence intestinal barrier integrity, inflammation, and other essential physiological processes; regulating the homeostasis of critical host metabolites, such as ceramides and cholesterol; and metabolizing xenobiotics derived from diet and drugs, thereby modulating nutrient absorption and drug efficacy.
Given the complexity of the functions of gut microbiota, it is arguably overly simplistic to categorize them as symbionts that are probiotic or pathogenic. Rather, by identifying and characterizing key microbial enzymes, we will be able to precisely modulate gut microbiota functions in health and disease. When a clear enzymatic cause is identified, therapies targeting microbial enzymes capitalize on a function-driven mechanism. This allows for precision that is independent of taxonomy and avoids off-target consequences stemming from compositional heterogeneity of the functional microbes across individuals. The operational feasibility and druggability of these therapies are further supported by mature enzyme-based therapy development paradigms. Ultimately, enzyme-targeted interventions are expected to work alongside conventional whole-microbiota or strain-level approaches, thereby enriching the toolkit for developing gut microbiome-based therapeutics.
