75 zero-days exploited in 2024, with 44% hitting enterprise tools and 34 tied to threat groups.
Category: security – Page 2
WhatsApp launches Private Processing using CVM and OHTTP, ensuring AI-driven message privacy and auditable security.
Multiple AI jailbreaks and tool poisoning flaws expose GenAI systems like GPT-4.1 and MCP to critical security risks.
Offensive Security warned Kali Linux users to manually install a new Kali repository signing key to avoid experiencing update failures.
The announcement comes after OffSec lost the old repo signing key (ED444FF07D8D0BF6) and was forced to create a new one (ED65462EC8D5E4C5) signed by Kali Linux developers using signatures available on the Ubuntu OpenPGP key server. However, since the key was not compromised, the old one was not removed from the keyring.
When trying to get the list of latest software packages on systems still using the old key, users will see “Missing key 827C8569F2518CC677FECA1AED65462EC8D5E4C5, which is needed to verify signature” errors.
ARMO shows io_uring-based rootkits evade Falco, Tetragon, and Defender, risking Linux runtime security.
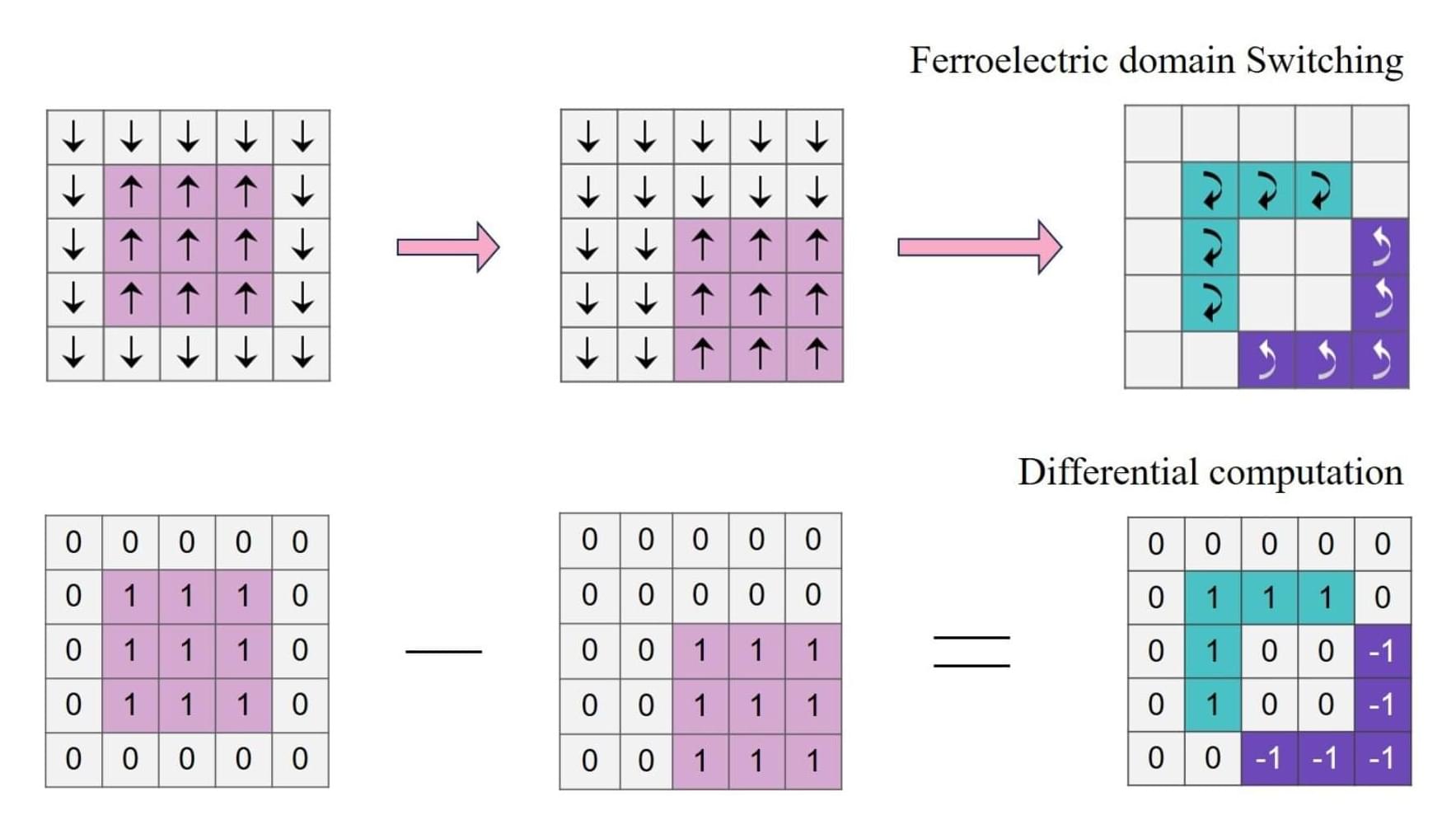
In a new Nature Communications study, researchers have developed an in-memory ferroelectric differentiator capable of performing calculations directly in the memory without requiring a separate processor.
The proposed differentiator promises energy efficiency, especially for edge devices like smartphones, autonomous vehicles, and security cameras.
Traditional approaches to tasks like image processing and motion detection involve multi-step energy-intensive processes. This begins with recording data, which is transmitted to a memory unit, which further transmits the data to a microcontroller unit to perform differential operations.
Microsoft on Monday announced that it has moved the Microsoft Account (MSA) signing service to Azure confidential virtual machines (VMs) and that it’s also in the process of migrating the Entra ID signing service as well.
The disclosure comes about seven months after the tech giant said it completed updates to Microsoft Entra ID and MS for both public and United States government clouds to generate, store, and automatically rotate access token signing keys using the Azure Managed Hardware Security Module (HSM) service.
“Each of these improvements helps mitigate the attack vectors that we suspect the actor used in the 2023 Storm-0558 attack on Microsoft,” Charlie Bell, Executive Vice President for Microsoft Security, said in a post shared with The Hacker News ahead of publication.
Microsoft has released the optional KB5055612 preview cumulative update for Windows 10 22H2 with two changes, including a fix for a GPU paravirtualization bug in Windows Subsystem for Linux 2 (WSL2).
The KB5055612 cumulative update preview is part of Microsoft’s “optional non-security preview updates” schedule, typically released at the end of every month. This update allows Windows admins to test upcoming fixes and features that will be released in the upcoming May Patch Tuesday.
Unlike Patch Tuesday cumulative updates, this preview update does not include security updates.
Given the complexity of multi-tenant cloud environments and the growing need for real-time threat mitigation, Security Operations Centers (SOCs) must adopt AI-driven adaptive defense mechanisms to counter Advanced Persistent Threats (APTs). However, SOC analysts face challenges in handling adaptive adversarial tactics, requiring intelligent decision-support frameworks. We propose a Cognitive Hierarchy Theory-driven Deep Q-Network (CHT-DQN) framework that models interactive decision-making between SOC analysts and AI-driven APT bots. The SOC analyst (defender) operates at cognitive level-1, anticipating attacker strategies, while the APT bot (attacker) follows a level-0 policy. By incorporating CHT into DQN, our framework enhances adaptive SOC defense using Attack Graph (AG)-based reinforcement learning. Simulation experiments across varying AG complexities show that CHT-DQN consistently achieves higher data protection and lower action discrepancies compared to standard DQN. A theoretical lower bound further confirms its superiority as AG complexity increases. A human-in-the-loop (HITL) evaluation on Amazon Mechanical Turk (MTurk) reveals that SOC analysts using CHT-DQN-derived transition probabilities align more closely with adaptive attackers, leading to better defense outcomes. Moreover, human behavior aligns with Prospect Theory (PT) and Cumulative Prospect Theory (CPT): participants are less likely to reselect failed actions and more likely to persist with successful ones. This asymmetry reflects amplified loss sensitivity and biased probability weighting — underestimating gains after failure and overestimating continued success. Our findings highlight the potential of integrating cognitive models into deep reinforcement learning to improve real-time SOC decision-making for cloud security.
In a rather clever attack, hackers leveraged a weakness that allowed them to send a fake email that seemed delivered from Google’s systems, passing all verifications but pointing to a fraudulent page that collected logins.
The attacker leveraged Google’s infrastructure to trick recipients into accessing a legitimate-looking “support portal” that asks for Google account credentials.
The fraudulent message appeared to come from “no-reply@google.com” and passed the DomainKeys Identified Mail (DKIM) authentication method but the real sender was different.