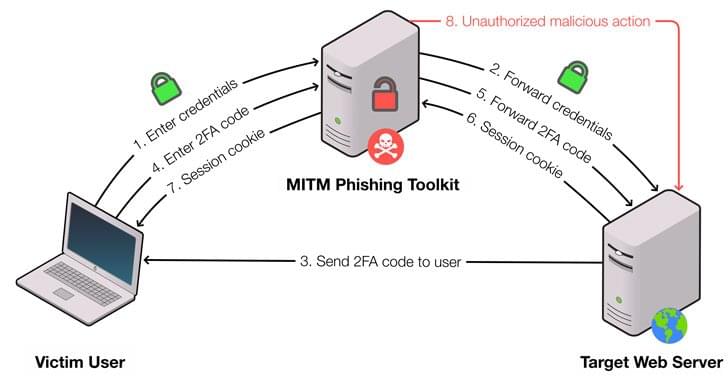
Researchers demonstrated new way to catch advanced MITM phishing toolkits in the wild.


The notorious Emotet malware is staging a comeback of sorts nearly 10 months after a coordinated law enforcement operation dismantled its command-and-control infrastructure in late January 2021.
According to a new report from security researcher Luca Ebach, the infamous TrickBot malware is being used as an entry point to distribute what appears to be a new version of Emotet on systems previously infected by the former. The latest variant takes the form of a DLL file, with the first occurrence of the deployment being detected on November 14.
And it can be hacked.
The authors of a new study in Nature Catalysis reprogrammed these blobs—called exosomes—into an army of living nanobioreactors. It’s a seemingly simple process of mix and match: each blob is filled with a different chemical that’s involved in a biological reaction. By bringing two together, the blobs merge into a single squishy container, allowing the two chemicals to react.
The results were explosive. The tiny bioreactors pumped out energy molecules, called ATP, inside living cells. The burst of energy saved injured cells, providing them with a boost of power to fight back against dangerous molecules that otherwise lead to cell death.

The TechCrunch Global Affairs Project examines the increasingly intertwined relationship between the tech sector and global politics.
Criminals have a long history of conducting cyber espionage on China’s behalf. Protected from prosecution by their affiliation with China’s Ministry of State Security (MSS), criminals turned government hackers conduct many of China’s espionage operations. Alarming as it may sound, this is not a new phenomenon. An indictment issued by the U.S. Department of Justice last year, for example, indicated that the simultaneous criminal-espionage activity of two Chinese hackers went back as far as 2009. In another case, FireEye, a cybersecurity company, alleges that APT41, a separate cohort of MSS hackers, began as a criminal outfit in 2012 and transitioned to concurrently conducting state espionage from 2014 onward. But there’s reason to believe that since then, China has been laying the groundwork for change.
A spate of policies beginning in 2015 put China in a position to replace contracted criminals with new blood from universities. The CCP’s first effort in 2015 was to standardize university cybersecurity degrees by taking inspiration from the United States’ National Initiative for Cybersecurity Education — a NIST framework for improving the U.S. talent pipeline. One year later, China announced the construction of a new National Cybersecurity Talent and Innovation Base in Wuhan. Including all of the Base’s components, it is capable of training and certifying 70,000 people a year in cybersecurity.



Many of the malware campaigns we have detected over the last year have been global at scale, targeting anyone with little regard to their location. Recently, we discovered and began monitoring the activity behind PhoneSpy, a spyware aimed at South Korean residents with Android devices. With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their devices.
Unlike other spyware campaigns we have covered that take advantage of vulnerabilities on the device, PhoneSpy hides in plain sight, disguising itself as a regular application with purposes ranging from learning Yoga to watching TV and videos, or browsing photos. But in reality, the application is stealing data, messages, images, and remote control of Android phones. The data stolen from victim devices ranged from personal photos to corporate communications. The victims were broadcasting their private information to the malicious actors with zero indication that something was amiss.
While the victims have been limited to South Korea, PhoneSpy is an example of how malicious applications can disguise their true intent. When installed on victims’ devices, they leave personal and corporate data at risk. With mobile devices playing critical roles in distributed and remote work, it is no surprise that spyware campaigns like PhoneSpy are on the rise.

Fighting ransomware with bounties.
In May, a ransomware attack shut down a pipeline carrying 45 percent of the fuel used on the US East Coast. The Colonial Pipeline incident led to panic buying and heightened fears about the threat posed by simple hacks to national infrastructure. Now, the US State Department is offering a bounty of up to $10 million to anyone who can supply the “identity or location” of the leaders of the group responsible — an outfit known as DarkSide.
In addition to the $10 million bounty, the state department is offering a reward of up to $5 million for information leading to the arrest or conviction “of any individual conspiring to participate in or attempting to participate in a DarkSide variant ransomware incident.” What exactly that means isn’t clear. Is a “DarkSide variant ransomware incident” one that involves the group’s hacking tools? What if the software has been altered slightly? It seems deliberately ambiguous, allowing the State Department to cast as wide a net as possible.