Jun 9, 2024
Thousands of companies using Ray framework exposed to cyberattacks, researchers say
Posted by Saúl Morales Rodriguéz in categories: cybercrime/malcode, robotics/AI
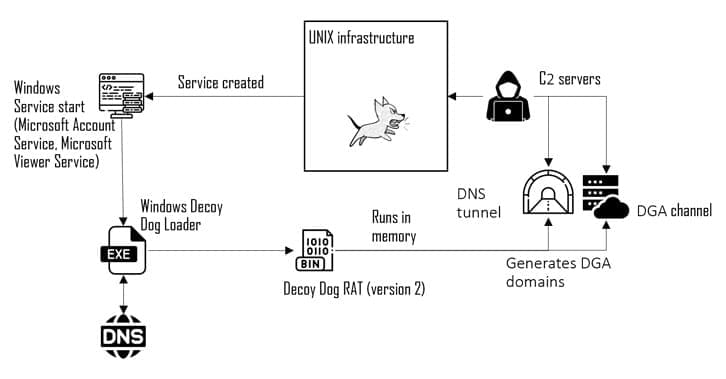
Researchers are warning that hackers are actively exploiting a disputed vulnerability in a popular open-source AI framework known as Ray.
This tool is commonly used to develop and deploy large-scale Python applications, particularly for tasks like machine learning, scientific computing and data processing.
According to Ray’s developer, Anyscale, the framework is used by major tech companies such as Uber, Amazon and OpenAI.





 עברית (Hebrew)
עברית (Hebrew)











