Jul 26, 2024
Google Chrome now asks for passwords to scan protected archives
Posted by Saúl Morales Rodriguéz in categories: cybercrime/malcode, internet
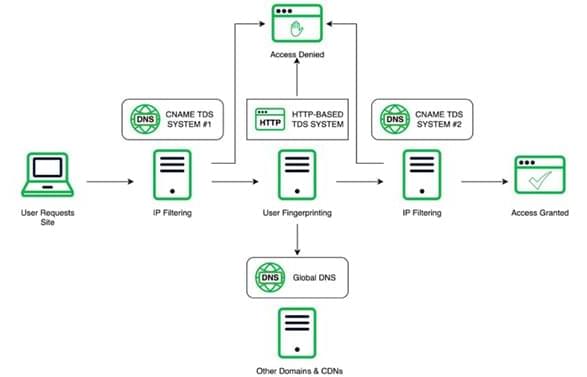
Google Chrome now warns when downloading risky password-protected files and provides improved alerts with more information about potentially malicious downloaded files.
These new, more detailed warning messages help users quickly learn the nature of the danger presented by each file downloaded from the Internet.
For this, Google introduced a two-tier download warning system that uses AI-powered malware verdicts sourced from its Safe Browsing service to help evaluate the actual risk quickly.