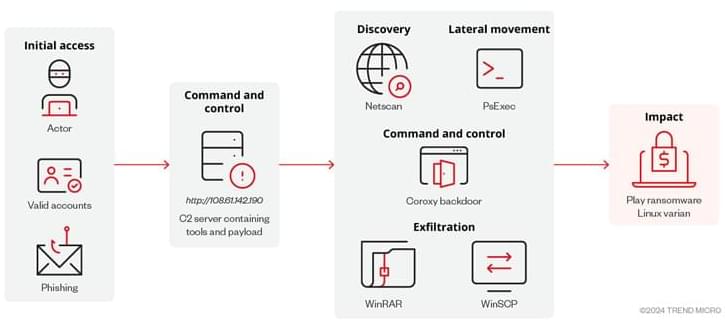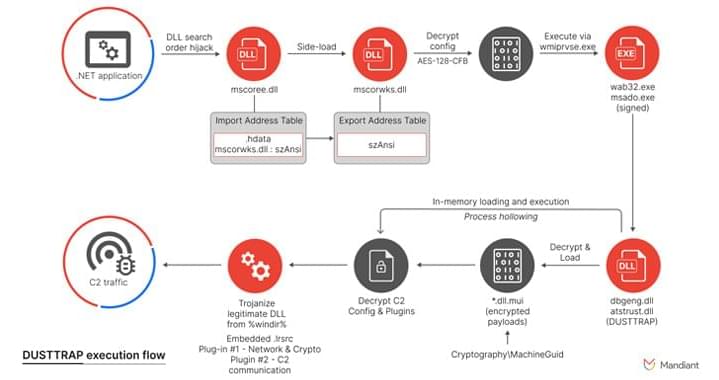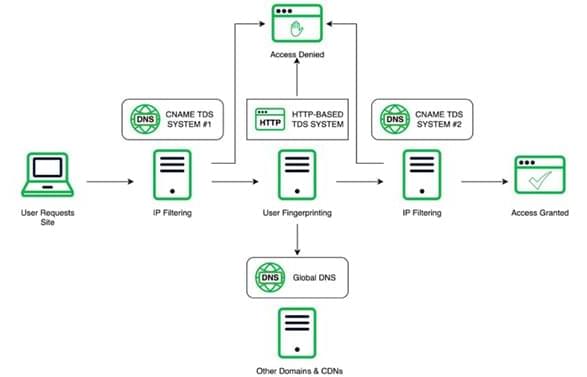
A Chinese organized crime syndicate with links to money laundering and human trafficking across Southeast Asia has been using an advanced “technology suite” that runs the whole cybercrime supply chain spectrum to spearhead its operations.
Infoblox is tracking the proprietor and maintainer under the moniker Vigorish Viper, noting that it’s developed by the Yabo Group (aka Yabo Sports), which has been linked to illegal gambling operations and pig butchering scams in the past. In late 2022, it rebranded as Kaiyun Sports and has since been absorbed into another newly formed entity called Ponymuah.
The suite, marketed in China as “baowang” (“包网,” meaning full package) encompasses several components such as Domain Name System (DNS) configurations, website hosting, payment mechanisms, advertising, and mobile apps. It also hosts thousands of domain names and numerous brands in an infrastructure that’s tied to Hong Kong and China.