Linux routers in Japan are the target of a new Golang remote access trojan (RAT) called GobRAT.
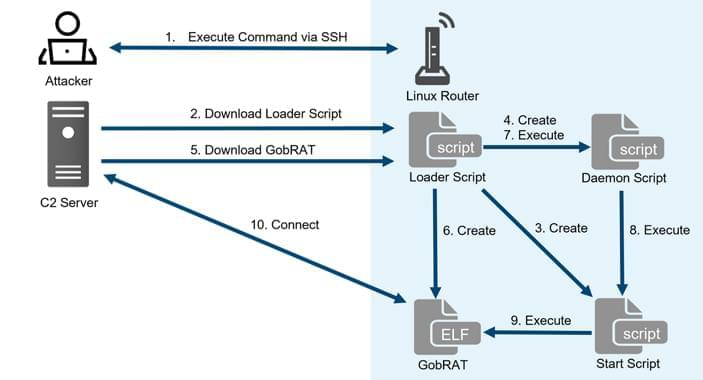
“Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT,” the JPCERT Coordination Center (JPCERT/CC) said in a report published today.
The compromise of an internet-exposed router is followed by the deployment of a loader script that acts as a conduit for delivering GobRAT, which, when launched, masquerades as the Apache daemon process (apached) to evade detection.