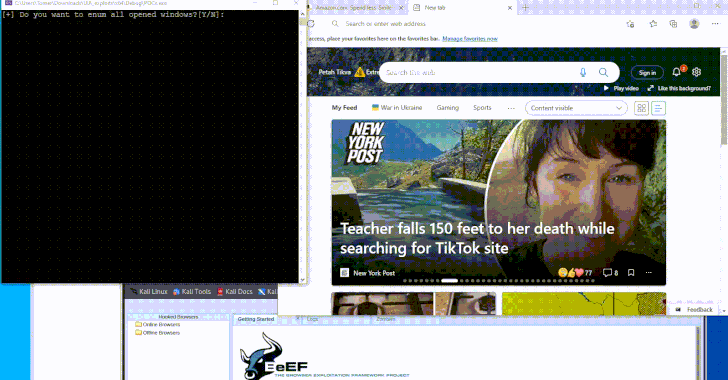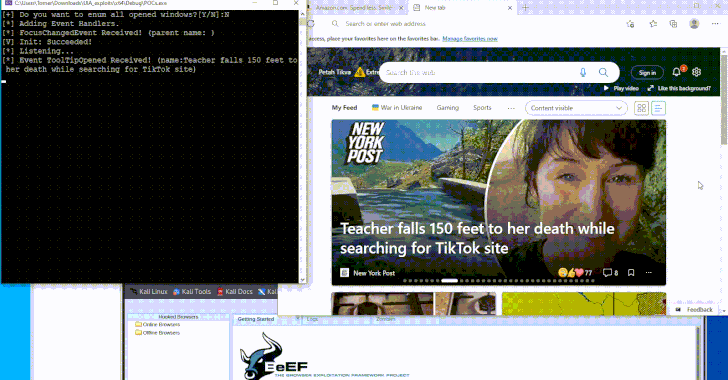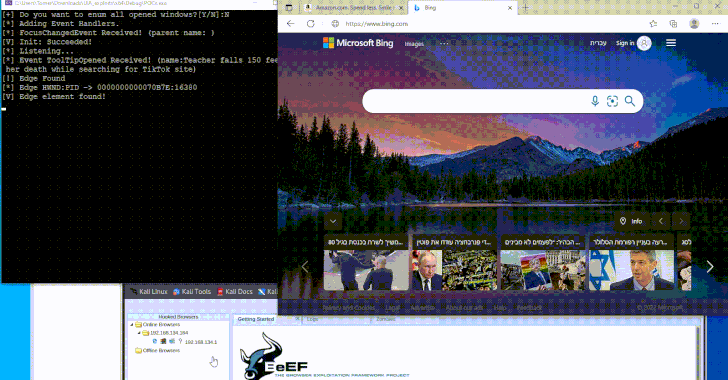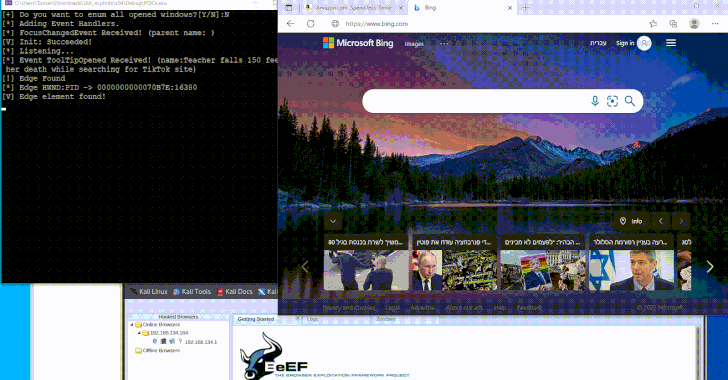
PowerOFF dismantles 27 DDoS stresser services, arrests administrators, and exposes CDN/WAF misconfiguration risks.
Category: cybercrime/malcode – Page 7
Secret Blizzard has a track record of targeting various sectors to facilitate long-term covert access for intelligence collection, but their primary focus is on ministries of foreign affairs, embassies, government offices, defense departments, and defense-related companies across the world.
The latest report comes a week after the tech giant, along with Lumen Technologies Black Lotus Labs, revealed Turla’s hijacking of 33 command-and-control (C2) servers of a Pakistan-based hacking group named Storm-0156 to carry out its own operations.
The attacks targeting Ukrainian entities entail commandeering Amadey bots to deploy a backdoor known as Tavdig, which is then used to install an updated version of Kazuar, which was documented by Palo Alto Networks Unit 42 in November 2023.
Windows UI Automation exploited to bypass EDR tools, enabling data theft, phishing, and app manipulation.
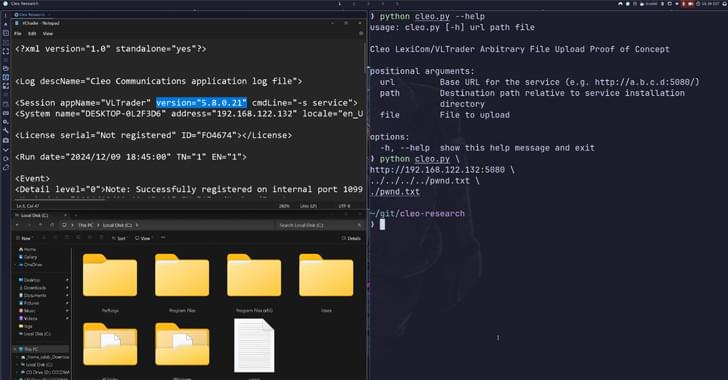
Critical Cleo software flaw exploited en masse; update Harmony, VLTrader, LexiCom to prevent ransomware attacks.
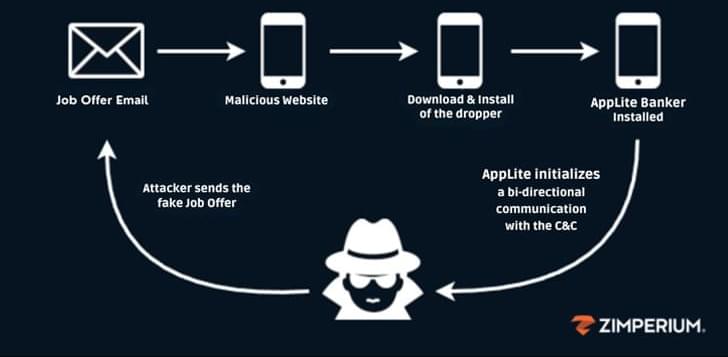
Updated Antidot banking trojan targets Android users via fake job offers, stealing credentials and taking remote control.
Phishing gang arrested in Belgium and Netherlands; Europol seizes luxury goods, cash, and millions stolen.
Humanity’s quest for answers has a new ally: Google’s Willow chip — a quantum chip that outpaces the fastest supercomputers by septillions of years! Imagine solving problems regular computers take years for—like creating life-saving medicines, predicting weather, or designing tech we haven’t dreamed of yet. But with great power comes challenges: high costs, logistics, and even risks to cybersecurity. The quantum revolution has begun, but the big question is—how will we use this power? Palki Sharma tells you.
Google | willow | quantum chip | firstpost | world news | news live | vantage | palki sharma | news.
#google #quantumchip #willow #firstpost #vantageonfirstpost #palkisharma #worldnews.
Vantage is a ground-breaking news, opinions, and current affairs show from Firstpost. Catering to a global audience, Vantage covers the biggest news stories from a 360-degree perspective, giving viewers a chance to assess the impact of world events through a uniquely Indian lens.
Mike has over 15 years of experience in healthcare, including extensive experience designing and developing medical devices. MedCrypt, Inc.
On October 1, 2024, the Food and Drug Administration (FDA) marked a major milestone in medical device cybersecurity enforcement. This marks one year since the retracted Refuse to Accept (RTA) policy and the full implementation of the Protecting and Transforming Cyber Healthcare (PATCH) Act amendment to the Food, Drug & Cosmetic Act (FD&C). The FDA’s new requirements represent a fundamental shift in the regulatory landscape for medical device manufacturers (MDMs), as cybersecurity is now a non-negotiable element of device development and compliance.
The timing is not coincidental. In 2023, the FDA issued its final guidance entitled “Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions.” This outlined the detailed cybersecurity requirements and considerations that MDMs must address in their submissions, highlighting the security measures in place to gain regulatory approval. With these requirements, the FDA is taking a hard stance: Cybersecurity is a core consideration, with compliance being systematically enforced.
Hackers Infect 8,000,000 Smartphones As ‘SpyLoan’ Drains Bank Accounts, Steals Sensitive Data for Extortion: McAfee Alert
Posted in cybercrime/malcode, finance, mobile phones | Leave a Comment on Hackers Infect 8,000,000 Smartphones As ‘SpyLoan’ Drains Bank Accounts, Steals Sensitive Data for Extortion: McAfee Alert
Cybersecurity firm McAfee says it’s identified a “significant global increase” in a smartphone hack that triggers extortion, harassment and drains bank accounts.
McAfee says hackers are increasingly deploying a group of malicious financial apps containing “SpyLoan” malware, posing a serious threat with more than eight million active installations around the world.
The apps are on Google Play and use the names, logos, brand colors and interfaces of well-known financial institutions.