Aug 27, 2023
Study highlights the vulnerabilities of metasurface-based wireless communication systems
Posted by Saúl Morales Rodriguéz in categories: cybercrime/malcode, internet
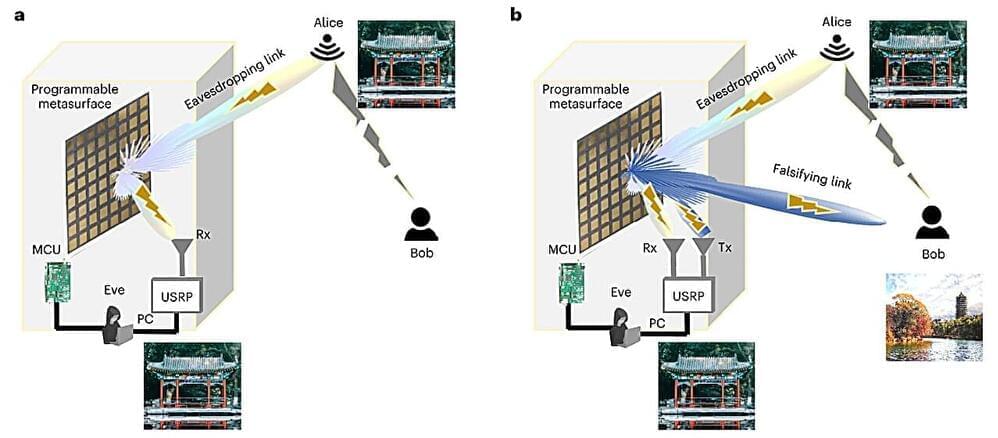
Metasurfaces, artificially engineered surfaces that can manipulate electromagnetic signals in unique ways, have huge potential for several technological applications, including the implementation of sixth generation (6G) cellular communications. The limitations and vulnerabilities of these smart surfaces, however, are still poorly understood.
Researchers at Peking University, University of Sannio and Southeast University recently carried out a study aimed at better understanding the vulnerability of metasurfaces to wireless cyber-attacks. Their paper, published in Nature Electronics, outlines two types of attacks that should be considered and accounted for before metasurfaces can be deployed on a large-scale.
“This work was primarily driven by the need for enhancing security and privacy of wireless communications in the upcoming 6G era, characterized by unprecedented speeds, ultra-low latency, and vast connection nodes,” Lianlin Li, Vincenzo Galdi and Tie Jun Cui, three of the researchers who carried out the study, told Tech Xplore.

 עברית (Hebrew)
עברית (Hebrew)