Page 961
Apr 30, 2024
The biggest myths about electric vehicles
Posted by Kelvin Dafiaghor in categories: sustainability, transportation
As electric vehicle (EV) sales skyrocket, more than doubling in 2021 compared to 2020, and automotive companies announce massive investments in batteries and EVs, the transition from gas to electricity-powered vehicles is looking all the more inevitable.
Still, misinformation abounds during this exciting technological change. Here are seven of the biggest myths about EVs.
1. Electric cars will always be more expensive. Up front electric vehicle prices have steadily fallen since the turn of the century, to the point where they are closing in on parity with gas vehicles.
Apr 29, 2024
A new approach to dark matter could help us solve galactic anomalies
Posted by Genevieve Klien in category: cosmology
Cosmological puzzles are tempting astronomers to rethink our simple picture of the universe – and ask whether dark matter is even stranger than we thought.
By Stuart Clark
Apr 29, 2024
Atlas, forefather of humanoid robots, gives way to next generation
Posted by Genevieve Klien in category: robotics/AI
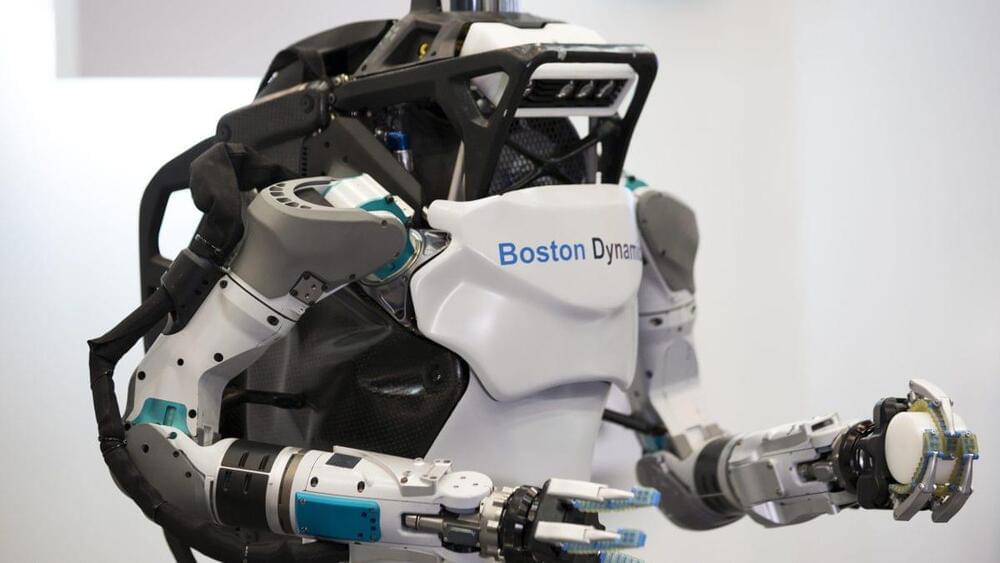
Boston Dynamics is retiring the original Atlas at the age of 11. TechCrunch’s Brian Heater discusses the pioneering bot’s legacy and what the company has in mind for its offspring.
Apr 29, 2024
Japan probe finds scars of micrometeoroid bombardment on asteroid Ryugu
Posted by Genevieve Klien in categories: robotics/AI, space
Direct sample analysis offers several advantages over robotic explorers conducting it from the surface of an asteroid or planet and then beaming back the data.
It provides a window into understanding how the surface of a celestial body has changed due to its constant exposure to the harsh deep space environment.
The scientists conducted their analysis using electron holography, a technique in which electron waves infiltrate materials. This method has the potential to uncover key details about the sample’s structure and magnetic and electric properties.
Apr 29, 2024
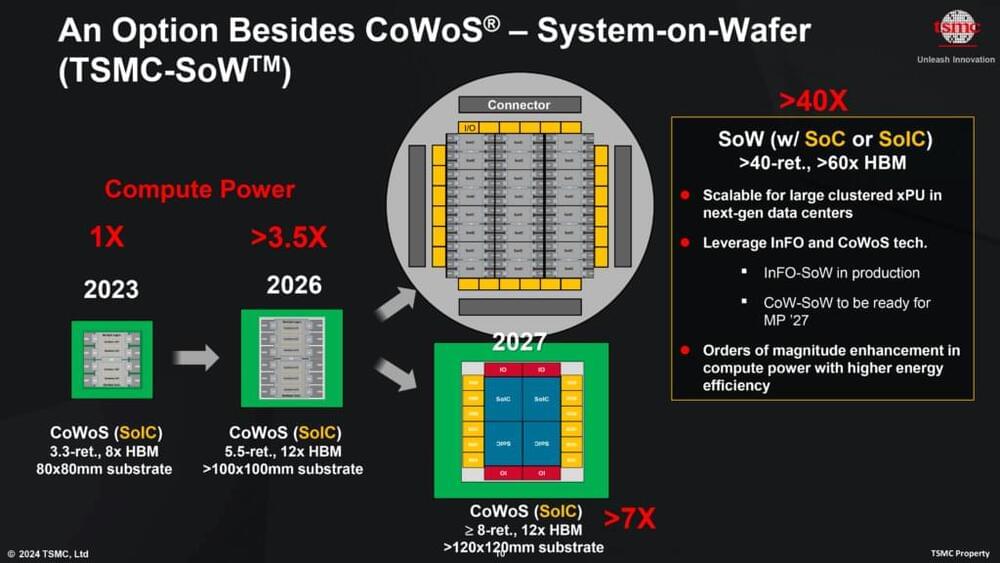
TSMC System on Wafer for Over 3.5 Times the Compute by 2027
Posted by Genevieve Klien in categories: innovation, robotics/AI
TSMC introduced its System-on-Wafer (TSMC-SoW™) technology, an innovative solution to bring revolutionary performance to the wafer level in addressing the future AI requirements for hyperscaler datacenters.
At the TSMC 2024 North America Technology Symposium, they debuted the TSMC A16™ technology, featuring leading nanosheet transistors with innovative backside power rail solution for production in 2026, bringing greatly improved logic density and performance.
The latest version of CoWoS allows TSMC to build silicon interposers that are about 3.3 times larger than the size of a photomask (or reticle, which is 858mm2). Thus, logic, eight HBM3/HBM3E memory stacks, I/O, and other chiplets can occupy up to 2,831 mm2. The maximum substrate size is 80×80 mm.
Apr 29, 2024
Account compromise of “unprecedented scale” uses everyday home devices
Posted by Genevieve Klien in category: cybercrime/malcode
Authentication service Okta is warning about the “unprecedented scale” of an ongoing campaign that routes fraudulent login requests through the mobile devices and browsers of everyday users in an attempt to conceal the malicious behavior.
The attack, Okta said, uses other means to camouflage the login attempts as well, including the TOR network and so-called proxy services from providers such as NSOCKS, Luminati, and DataImpulse, which can also harness users’ devices without their knowledge. In some cases, the affected mobile devices are running malicious apps. In other cases, users have enrolled their devices in proxy services in exchange for various incentives.
Unidentified adversaries then use these devices in credential-stuffing attacks, which use large lists of login credentials obtained from previous data breaches in an attempt to access online accounts. Because the requests come from IP addresses and devices with good reputations, network security devices don’t give them the same level of scrutiny as logins from virtual private servers (VPS) that come from hosting services threat actors have used for years.
Apr 29, 2024
Billion-Dollar Bank Facing Class Action Compliant After Data Breach Exposes Customers’ Names, Social Security Numbers and Other Sensitive Information
Posted by Genevieve Klien in categories: cybercrime/malcode, finance
A US bank is facing a proposed class action lawsuit for allegedly failing to protect its customers’ sensitive personal information and suffering a massive data breach.
SouthState Bank, which has over $45 billion in assets, is being hit with a class action lawsuit led by plaintiff Latonya Gore in Florida, filings show.
The suit concerns a February 2024 data breach that compromised the banks’ clients’ full names, financial account numbers and Social Security numbers.
Apr 29, 2024
Millions of devices still vulnerable to abandoned USB worm, continues to spread globally
Posted by Genevieve Klien in category: cybercrime/malcode
Security researchers have uncovered a chilling global epidemic: an old malware that has been spreading uncontrollably for years. Despite its creators seemingly abandoning the project years ago, this insidious USB worm has lived on, potentially infecting millions of new machines around the world.
The worm, which first hit the scene in 2019 as a new variant of the infamous PlugX malware, had a devious trick up its sleeve. It could automatically copy itself onto any USB drive connected to an infected machine, allowing it to hitch a ride and infect new computers without any user interaction required.
But at some point, the hackers abandoned the malware’s command-and-control server, essentially cutting off their ability to oversee the infected machines. One might assume this would be the end of the line for the pesky worm, but that was not the case.