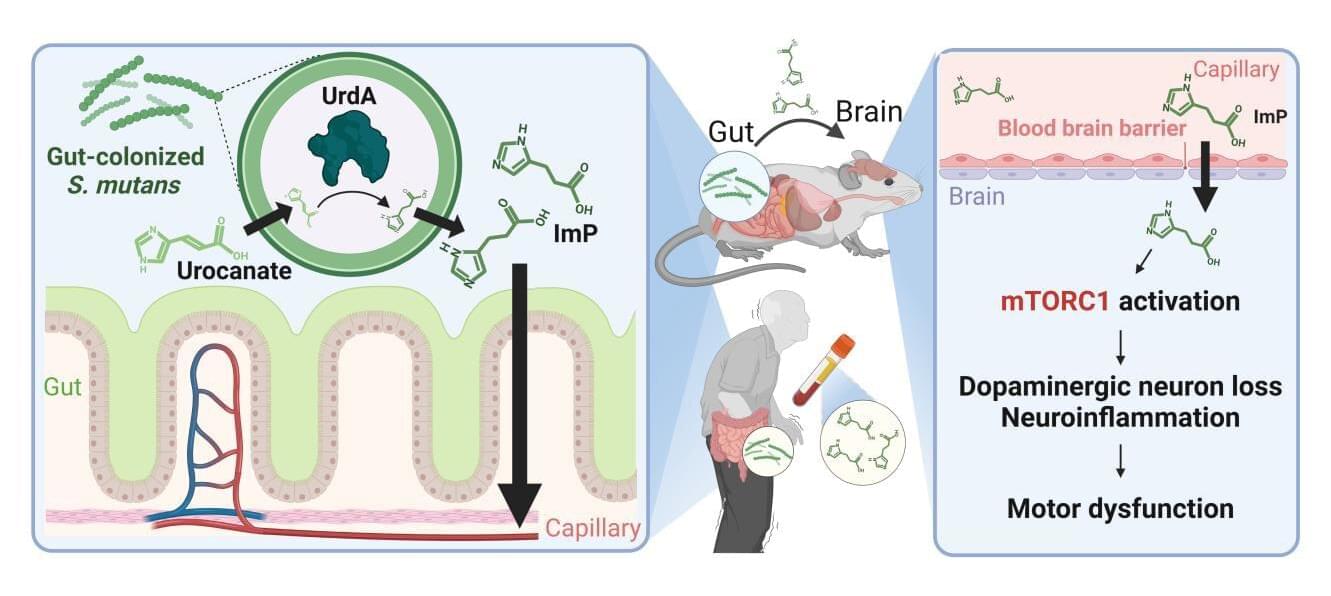
Korean researchers have uncovered compelling evidence that oral bacteria, once colonized in the gut, can affect neurons in the brain and potentially trigger Parkinson’s disease.
The joint research team, led by Professor Ara Koh and doctoral candidate Hyunji Park of POSTECH’s Department of Life Sciences, together with Professor Yunjong Lee and doctoral candidate Jiwon Cheon of Sungkyunkwan University School of Medicine, collaborated with Professor Han-Joon Kim of Seoul National University College of Medicine.
They have identified the mechanism by which metabolites produced by oral bacteria in the gut may trigger the development of Parkinson’s disease. The findings were published online in Nature Communications.