Page 769
May 30, 2024
CISA Alerts Federal Agencies to Patch Actively Exploited Linux Kernel Flaw
Posted by Saúl Morales Rodriguéz in category: cybercrime/malcode
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Linux kernel to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
Tracked as CVE-2024–1086 (CVSS score: 7.8), the high-severity issue relates to a use-after-free bug in the netfilter component that permits a local attacker to elevate privileges from a regular user to root and possibly execute arbitrary code.
“Linux kernel contains a use-after-free vulnerability in the netfilter: nf_tables component that allows an attacker to achieve local privilege escalation,” CISA said.
May 30, 2024
Cyber Espionage Alert: LilacSquid Targets IT, Energy, and Pharma Sectors
Posted by Saúl Morales Rodriguéz in category: energy
A previously undocumented cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various sectors in the United States (U.S.), Europe, and Asia as part of a data theft campaign since at least 2021.
“The campaign is geared toward establishing long-term access to compromised victim organizations to enable LilacSquid to siphon data of interest to attacker-controlled servers,” Cisco Talos researcher Asheer Malhotra said in a new technical report published today.
Targets include information technology organizations building software for the research and industrial sectors in the U.S, energy companies in Europe, and the pharmaceutical sector in Asia, indicating a broad victimology footprint.
May 30, 2024
Spider-Inspired Microphone Detects Tiny Gusts of Sound
Posted by Saúl Morales Rodriguéz in category: computing
A small device senses sounds using a spiderweb-like design—a strategy that could lead to chip-size microphones that are less affected by thermal noise.
Experiments and numerical simulations indicate that randomly replacing a few nonmagnetic components with magnetic ones in a photonic alloy induces backscattering-free light propagation along its edge.
May 30, 2024
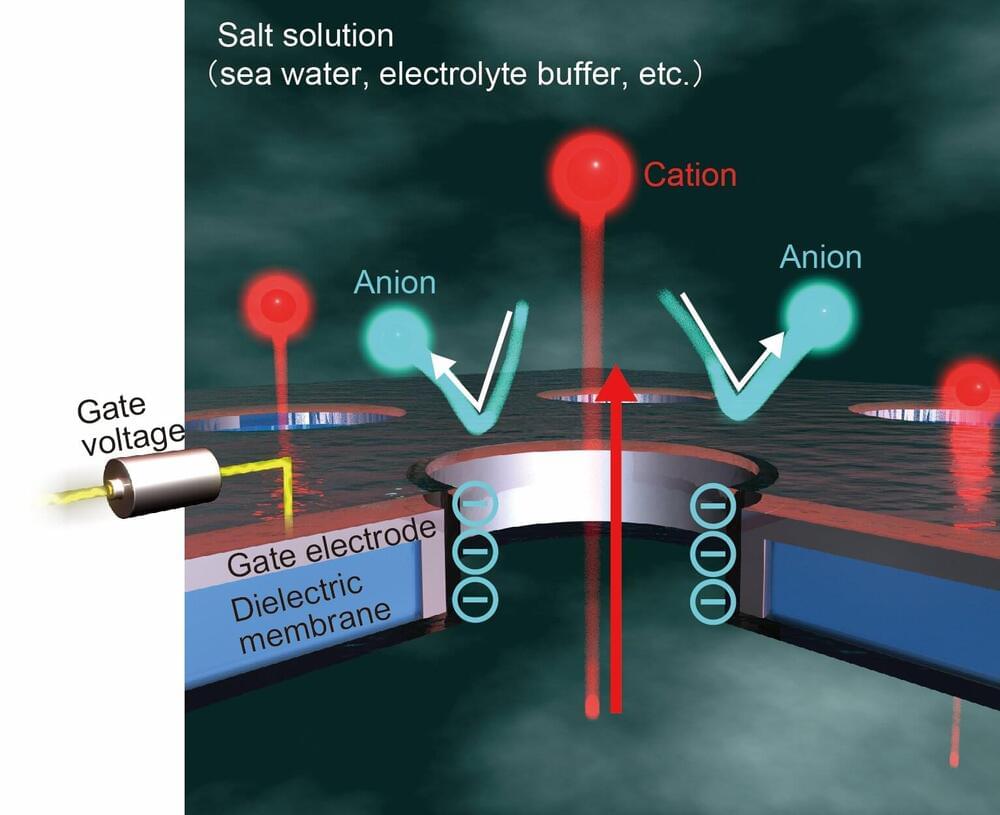
Controlling ion transport for a blue energy future: Research highlights the potential of nanopore membranes
Posted by Saúl Morales Rodriguéz in categories: energy, sustainability
Blue energy has the potential to provide a sustainable alternative to fossil fuels. In simple terms, it involves harnessing the energy produced when the ions in a salt solution move from high to low concentrations.
May 30, 2024
Simulations demonstrate potential mechanisms of intermediate-mass black hole formation in globular clusters
Posted by Saúl Morales Rodriguéz in category: cosmology
Joint research led by Michiko Fujii of the University of Tokyo demonstrates a possible formation mechanism of intermediate-mass black holes in globular clusters, star clusters that could contain tens of thousands or even millions of tightly packed stars.
May 30, 2024
Data-driven model generates natural human motions for virtual avatars
Posted by Saúl Morales Rodriguéz in category: robotics/AI
Humans can innately perform a wide range of movements, as this allows them to best tackle various tasks in their day-to-day life. Automatically reproducing these motions in virtual avatars and 3D animated human-like characters could be highly advantageous for many applications, ranging from metaverse spaces to digital entertainment, AI interfaces and robotics.
Researchers at Max Planck Institute for Intelligent Systems and ETH Zurich recently developed WANDR, a new model that can generate natural human motions for avatars. This model, to be introduced in a paper presented at the Conference on Computer Vision and Pattern Recognition (CVPR 2024) in June, unifies different data sources under a single model to attain more realistic motions in 3D humanoid characters. The paper is also posted to the arXiv preprint server.
“At a high-level, our research aims at figuring out what it takes to create virtual humans able to behave like us,” Markos Diomataris, first author of the paper, told Tech Xplore. “This essentially means learning to reason about the world, how to move in it, setting goals and trying to achieve them.
May 30, 2024
‘Metaholograms’: Researchers develop a new type of hologram
Posted by Saúl Morales Rodriguéz in categories: augmented reality, encryption, holograms, security, virtual reality
This innovation has the potential to significantly improve AR/VR displays by enabling the projection of more complex and realistic scenes. It also holds promise for applications in image encryption, where the information is encoded into multiple holographic channels for enhanced security.
The research is a significant step forward in developing high-performance metaholograms with a vastly increased information capacity. This study paves the way for exciting new possibilities in various fields, from advanced displays to information encryption and information storage.
May 30, 2024
New study is step towards energy-efficient quantum computing in magnets
Posted by Saúl Morales Rodriguéz in categories: computing, nanotechnology, quantum physics
Researchers from Lancaster University and Radboud University Nijmegen have managed to generate propagating spin waves at the nanoscale and discovered a novel pathway to modulate and amplify them.