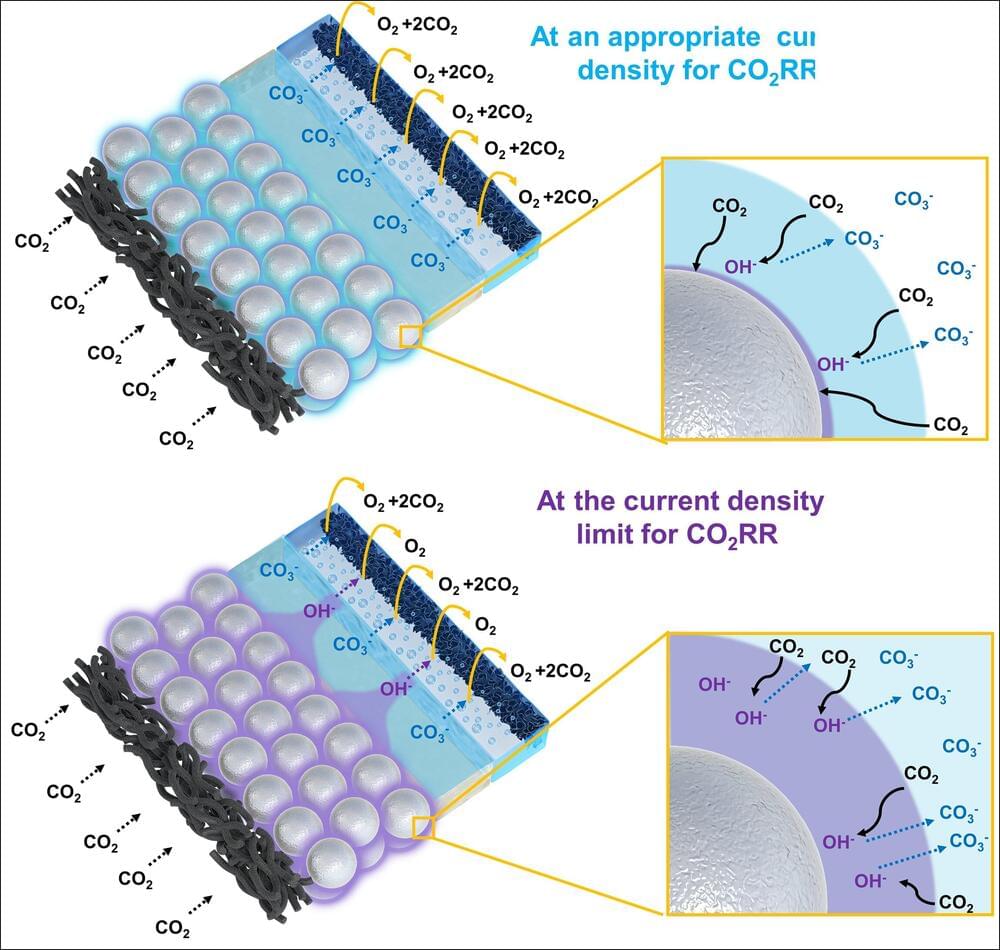
A research team led by Lund University in Sweden has developed an AI tool that traces back the most recent places you have been to.
Microorganisms are organisms, such as bacteria, that are invisible to the naked eye. The word microbiome is used to describe all the microorganisms in a particular environment. Establishing the geographical source of a microbiome sample has been a considerable challenge up to now.
However, in a new study, published in the research journal Genome Biology and Evolution, a research team presents the tool Microbiome Geographic Population Structure (mGPS). It is a unique instrument that uses ground-breaking AI technology to localise samples to specific bodies or water, countries and cities. The researchers discovered that many places have unique bacteria populations, so when you touch a handrail at a train station or bus stop, you pick up bacteria that can then be used to link you back to the exact place.
“In contrast to human DNA, the human microbiome changes constantly when we come into contact with different environments. By tracing where your microorganisms have been recently, we can understand the spread of disease, identify potential sources of infection and localise the emergence of microbial resistance. This tracing also provides forensic keys that can be used in criminal investigations,” says Eran Elhaik, biology researcher at Lund University, who led the new study.