Archive for the ‘mobile phones’ category: Page 77
Aug 31, 2022
Researchers use infrared light to wirelessly transmit power over 30 meters
Posted by Gemechu Taye in categories: electronics, mobile phones
We might be too close to wirelessly charging our mobile devices anywhere.
Researchers from Sejong University have developed a new system to transmit power over 30 meters using infrared light wirelessly. During laboratory tests, researchers demonstrated that the new system could transfer 400 mW of light power. For now, this amount of power is enough for charging sensors; however, further progress could mean enough high levels to charge mobile phones in various public places.
The research has been published in Optics Express.
Continue reading “Researchers use infrared light to wirelessly transmit power over 30 meters” »
Aug 31, 2022
Excessive blue light from our gadgets may accelerate the aging process
Posted by Saúl Morales Rodriguéz in categories: biotech/medical, chemistry, computing, mobile phones, neuroscience
Too much screen use has been linked to obesity and psychological problems. Now a new study has identified a new problem—a study in fruit flies suggests our basic cellular functions could be impacted by the blue light emitted by these devices. These results are published in Frontiers in Aging.
“Excessive exposure to blue light from everyday devices, such as TVs, laptops, and phones, may have detrimental effects on a wide range of cells in our body, from skin and fat cells, to sensory neurons,” said Dr. Jadwiga Giebultowicz, a professor at the Department of Integrative Biology at Oregon State University and senior author of this study. “We are the first to show that the levels of specific metabolites—chemicals that are essential for cells to function correctly—are altered in fruit flies exposed to blue light.”
“Our study suggests that avoidance of excessive blue light exposure may be a good anti-aging strategy,” advised Giebultowicz.
Aug 30, 2022
FTC Sues Data Broker Over Selling Location Data for Hundreds of Millions of Phones
Posted by Saúl Morales Rodriguéz in category: mobile phones
The U.S. Federal Trade Commission (FTC) on Monday said it filed a lawsuit against Kochava, a location data broker, for collecting and selling precise geolocation data gathered from consumers’ mobile devices.
The complaint alleges that the U.S. company amasses a “wealth of information” about users by purchasing data from other data brokers to sell to its own clients.
“Kochava then sells customized data feeds to its clients to, among other purposes, assist in advertising and analyzing foot traffic at stores or other locations,” the FTC said. “Among other categories, Kochava sells timestamped latitude and longitude coordinates showing the location of mobile devices.”
Aug 27, 2022
Highly Sensitive, Mass Producible Organic Photodetectors for Medical Sensors, Fingerprint Recognition
Posted by Saúl Morales Rodriguéz in categories: biotech/medical, mobile phones
New green-light absorbing photodetectors could be useful for medical sensors, fingerprint recognition, and more.
New green-light absorbing transparent organic photodetectors that are highly sensitive and compatible with CMOS fabrication methods have been developed and demonstrated by researchers. Incorporating these new photodetectors into organic-silicon hybrid image sensors could be useful for many applications. These include light-based heart-rate monitoring, fingerprint recognition, and devices that detect the presence of nearby objects.
Whether used in scientific cameras or smartphones, most of today’s imaging sensors are based on CMOS technology and inorganic photodetectors that convert light signals into electric signals. Although photodetectors made from organic materials are attracting attention because they can help boost sensitivity, for example, it has thus far proven difficult to fabricate high-performance organic photodetectors.
Aug 26, 2022
T‑Mobile Takes Coverage Above and Beyond With SpaceX
Posted by Gemechu Taye in categories: Elon Musk, mobile phones, satellites
Ending cellular dead zones in the U.S. is the ultimate goal.
Cellular service provider T-Mobile has teamed up with Elon Musk’s SpaceX to provide universal coverage using the constellation of Starlink satellites, a press release reveals.
Cellular services have gone through many iterations since their first roll-out. Most countries around the world are currently seeing a roll-out of the fifth generation (5G) of mobile connections that allows the bandwidth for high-speed gaming and streaming high-definition videos.
Continue reading “T‑Mobile Takes Coverage Above and Beyond With SpaceX” »
Aug 26, 2022
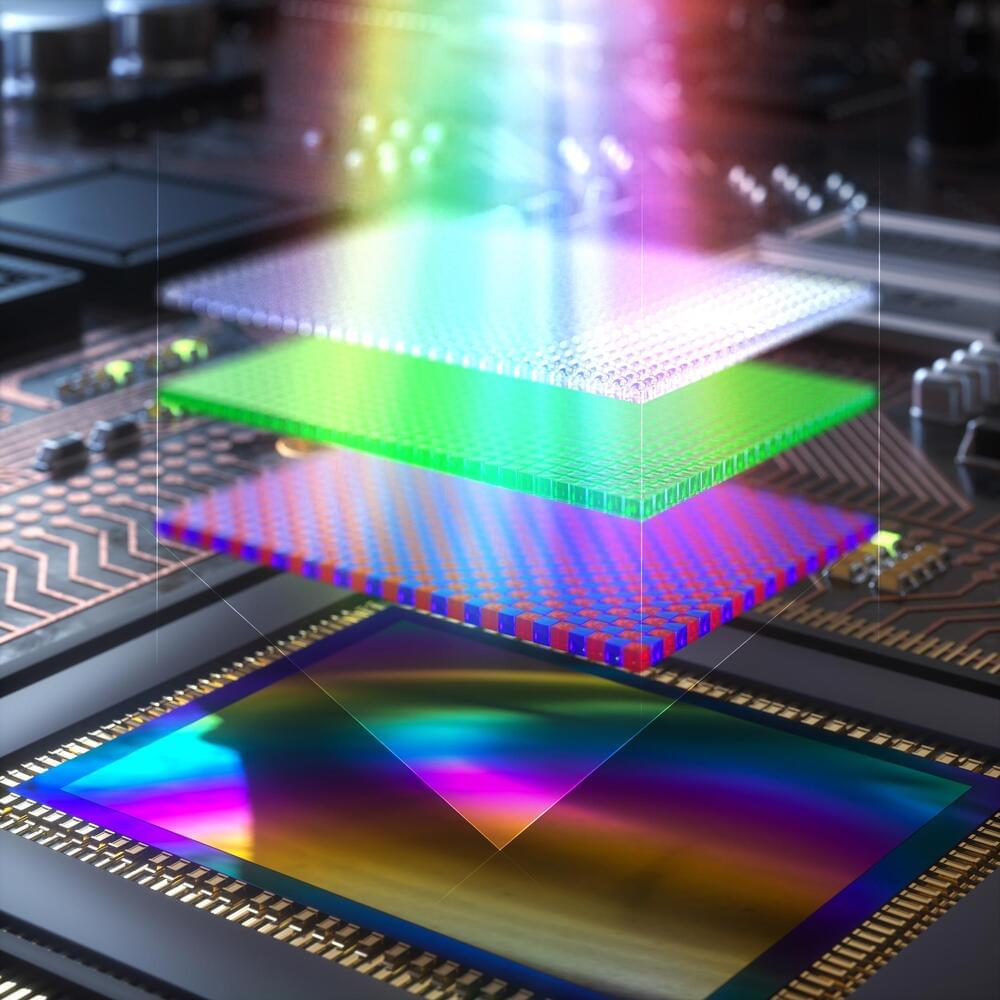
A silicon image sensor that computes
Posted by Shubham Ghosh Roy in categories: mobile phones, robotics/AI, transportation
As any driver knows, accidents can happen in the blink of an eye—so when it comes to the camera system in autonomous vehicles, processing time is critical. The time that it takes for the system to snap an image and deliver the data to the microprocessor for image processing could mean the difference between avoiding an obstacle or getting into a major accident.
In-sensor image processing, in which important features are extracted from raw data by the image sensor itself instead of the separate microprocessor, can speed up the visual processing. To date, demonstrations of in-sensor processing have been limited to emerging research materials which are, at least for now, difficult to incorporate into commercial systems.
Now, researchers from the Harvard John A. Paulson School of Engineering and Applied Sciences (SEAS) have developed the first in-sensor processor that could be integrated into commercial silicon imaging sensor chips–known as complementary metal-oxide-semiconductor (CMOS) image sensors–that are used in nearly all commercial devices that need capture visual information, including smartphones.
Aug 24, 2022
Researchers engineer novel material capable of ‘thinking’
Posted by Saúl Morales Rodriguéz in categories: biotech/medical, mobile phones, robotics/AI

Someone taps your shoulder. The organized touch receptors in your skin send a message to your brain, which processes the information and directs you to look left, in the direction of the tap. Now, Penn State and U.S. Air Force researchers have harnessed this processing of mechanical information and integrated it into engineered materials that “think”.
The work, published today in Nature, hinges on a novel, reconfigurable alternative to integrated circuits. Integrated circuits are typically composed of multiple electronic components housed on a single semiconductor material, usually silicon, and they run all types of modern electronics, including phones, cars and robots. Integrated circuits are scientists’ realization of information processing similar to the brain’s role in the human body. According to principal investigator Ryan Harne, James F. Will Career Development Associate Professor of Mechanical Engineering at Penn State, integrated circuits are the core constituent needed for scalable computing of signals and information but have never before been realized by scientists in any composition other than silicon semiconductors.
Continue reading “Researchers engineer novel material capable of ‘thinking’” »
Aug 24, 2022
Apple’s ‘Far Out’ iPhone event is scheduled for September 7th
Posted by Tristan Hambling in categories: computing, mobile phones
It’s official: Apple has just sent out invites for its next hardware event. As expected, the company will share what it’s been working on for the past year on September 7th, with a live broadcast from Apple Park starting at 1PM ET. The invite features the words “Far out.” Make of that what you will.
The company is widely expected to announce four new iPhone models at the event. Leading up to today’s announcement, most reports have suggested the 2022 iPhone lineup will consist of a 6.1-inch iPhone 14, a 6.7-inch iPhone 14 Max, a 6.1-inch iPhone 14 Pro and a 6.7-inch iPhone 14 Pro Max. Apple reportedly won’t offer a new “mini” model this year due to lackluster sales of the iPhone 12 mini and iPhone 13 mini.
Enhancements on the standard iPhone 14 models reportedly include the addition of more RAM, longer-lasting batteries and a better selfie camera with autofocus. Meanwhile, the Pro models are expected to feature a new design that trades away Apple’s signature display notch for a Samsung-style hole-punch front camera cutout. Additionally, the Pro variants will reportedly feature a new 48-megapixel main camera and thinner display bezels. They’re also expected to be the only models to ship with Apple’s next-generation A16 chip.
Aug 21, 2022
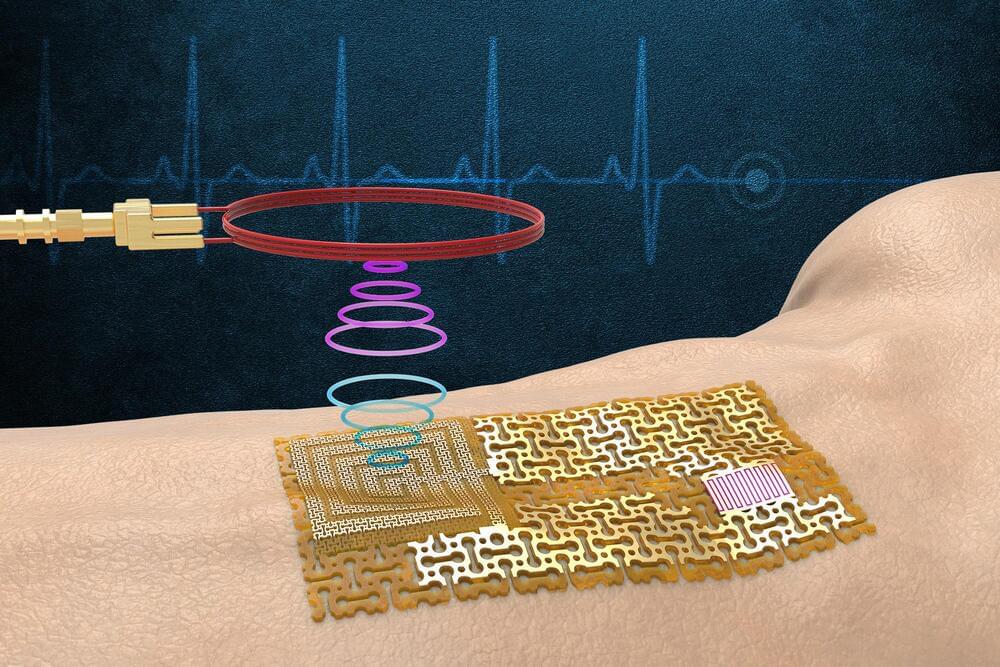
Engineers fabricate a chip-free, wireless, electronic ‘skin’
Posted by Saúl Morales Rodriguéz in categories: computing, mobile phones, wearables
Wearable sensors are ubiquitous thanks to wireless technology that enables a person’s glucose concentrations, blood pressure, heart rate, and activity levels to be transmitted seamlessly from sensor to smartphone for further analysis.
Most wireless sensors today communicate via embedded Bluetooth chips that are themselves powered by small batteries. But these conventional chips and power sources will likely be too bulky for next-generation sensors, which are taking on smaller, thinner, more flexible forms.
Now MIT engineers have devised a new kind of wearable sensor that communicates wirelessly without requiring onboard chips or batteries. Their design, detailed in the journal Science, opens a path toward chip-free wireless sensors.