Sep 27, 2019
Jumping the gap may make electronics faster
Posted by Saúl Morales Rodriguéz in categories: biotech/medical, computing, mobile phones, security, transportation
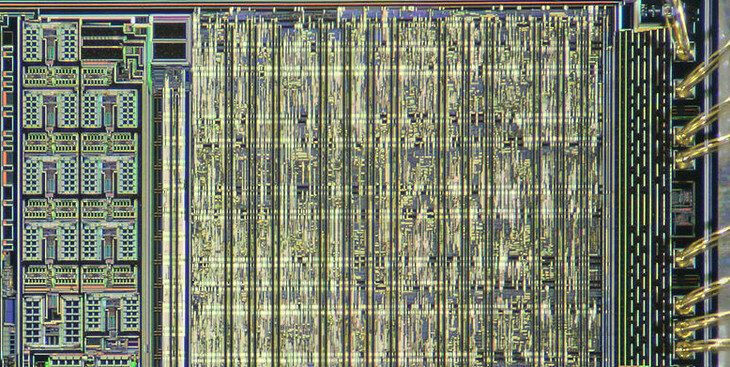
A quasi-particle that travels along the interface of a metal and dielectric material may be the solution to problems caused by shrinking electronic components, according to an international team of engineers.
“Microelectronic chips are ubiquitous today,” said Akhlesh Lakhtakia, Evan Pugh University Professor and Charles Godfrey Binder Professor of Engineering Science and Mechanics, Penn State. “Delay time for signal propagation in metal-wire interconnects, electrical loss in metals leading to temperature rise, and cross-talk between neighboring interconnects arising from miniaturization and densification limits the speed of these chips.”
These electronic components are in our smartphones, tablets, computers and security systems and they are used in hospital equipment, defense installations and our transportation infrastructure.