New “metaholograms” could transform AR/VR technologies by enabling crosstalk-free, high-fidelity image projection with vastly increased information capacity.
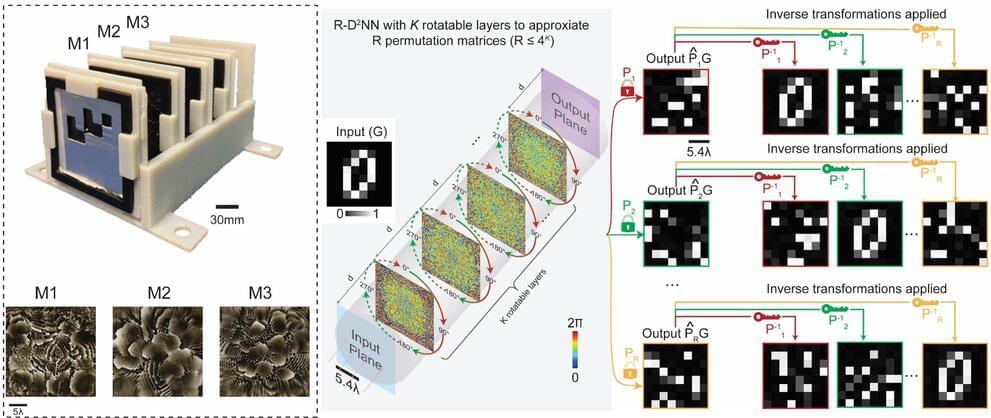
Researchers have developed a new type of holograms, known as “metaholograms,” capable of projecting multiple high-fidelity images free of crosstalk. This innovation opens doors to advanced applications in virtual and augmented reality (AR/VR) displays, data storage, and image encryption.
Metaholograms offer several advantages over traditional holograms, including broader operational bandwidth, higher imaging resolution, wider viewing angle, and more compact size. However, a major challenge for metaholograms has been their limited information capacity which only allows them to project a few independent images. Existing methods typically can provide a small number of display channels and often suffer from inter-channel crosstalk during image projections.