The ubiquity of electronic devices makes it essential to use encryption and anti-counterfeiting tools to protect the privacy and security of users. With the growing expansion of the Internet of Things, protection against attacks that violate the authenticity of products is increasingly necessary. Traditionally, message protection has been based on different systems: passwords, digital signatures or encryption. This cryptography is based on unknown keys to a possible attacker, but unfortunately these systems are becoming obsolete as new more invasive attacks appear: malware, API attacks or physical hardware attacks.
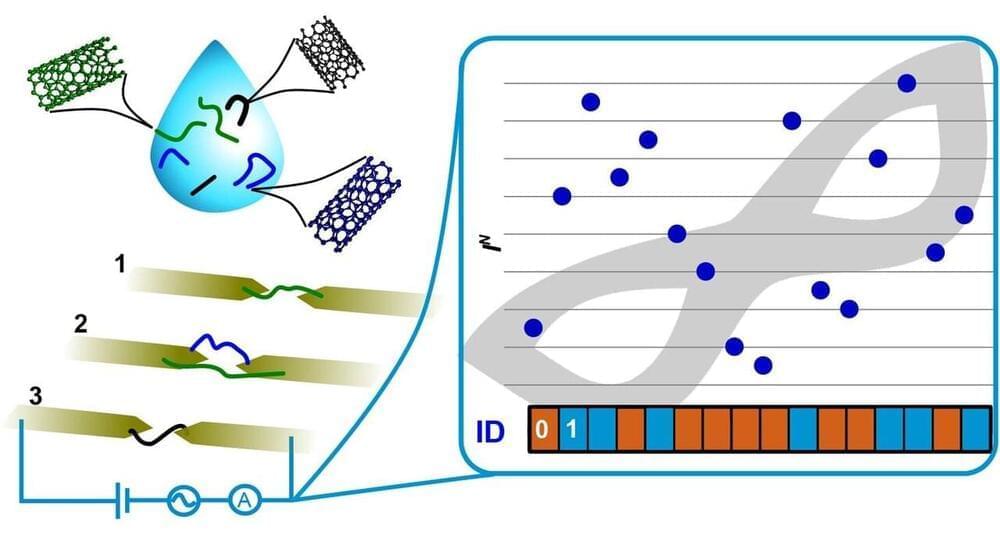
While quantum computing slowly progresses towards the cryptographic paradigm, the so-called physically unclonable functions (PUFs) are presented as the choice to ensure unique and effective identification. A PUF is a device that has unique and non-repeatable physical properties that can be translated into usable bits of information. The idea of applying random physical characteristics to identify systems or people is not new: for example, the identification of individuals using the fingerprint dates from the 19th century. More recently, the identity of electronic devices has been established using PUFs, which are “electronic fingerprints” of an integrated circuit.
Authentication based on PUFs comprises a chip manufactured by intrinsically random processes that make cloning almost impossible, even though all the details of the manufacturing process are known. The measurements of the various physical properties of the PUF depend on the properties of the chip at the nanoscale, thus constitute a very powerful anti-fraud and anti-counterfeiting technology. To be implementable at an industrial level, this chip must be low cost, scalable and its properties must be easily measurable by means of an identifiable function.







 עברית (Hebrew)
עברית (Hebrew)








